Cybersecurity News

How Smarter Social Engineering Tactics are Reshaping Cybersecurity – Insights from Our Own Steve Stasiukonis
Featured on Dark Reading: Our President Weighs in on the Evolution of Digital Deception Social engineering is evolving — and so are the criminals behind it. In a recent piece published on Dark Reading, our...

Hacked for the Holidays
Kick off your shoes, turn on the game, put your feet up. Crack a cold one, wait for family and friends to arrive (maybe via zoom given the circumstances) and bask in the few moments of reprieve from running...

Protect Your Business with Risk-Based Penetration Testing
Cybersecurity threats are on the rise, and organizations of all sizes are vulnerable to attacks. Hackers are constantly looking for ways to exploit vulnerabilities in your systems and applications, and the...
Company News

How Smarter Social Engineering Tactics are Reshaping Cybersecurity – Insights from Our Own Steve Stasiukonis
Featured on Dark Reading: Our President Weighs in on the Evolution of Digital Deception Social engineering is evolving — and so are the criminals behind it. In a recent piece published on Dark Reading, our...

Authentic8 Podcast Features Secure Network – Breaking In: How to Use OSINT for Pen Testing
https://www.youtube.com/watch?v=PL0fmFQiZOw Authentic8 recently featured Secure Network's Steve Stasiukonis on how OSINT can be used effectively for Penetration Testing. Recently, Authentic8 featured Secure...

MHEDA Journal – A Desire to Learn
Throughout her varied career, Megan Cardish has prioritized one goal, no matter the industry or job: to learn as much as she possibly can. After she graduated from college and started working for a real...
HACKER’S DICTIONARY
Sign Up to Get the H4X0R Word of the Month Delivered to Your Inbox
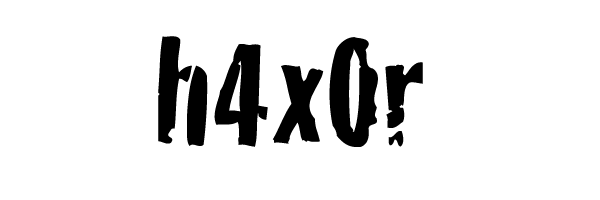
H4X0R
verb - hâx•ŏr Some nerdy kid who didn’t get enough attention as a child so they decided to learn how to break things. Often begins as a pastime, way to impress chicks or to win (cheat) at video games.What angry pre-teens call people who are better than them at...

PWNED
verb - pō•nd What happens when you're an older person that tried their hand at Modern Warfare with their niece/nephew/child for the first time and they take you out 37 rounds in a row.You've been seriously hacked. Totally owned. In other words, pwned. "Your network is...